Netzwerk-Konfiguration
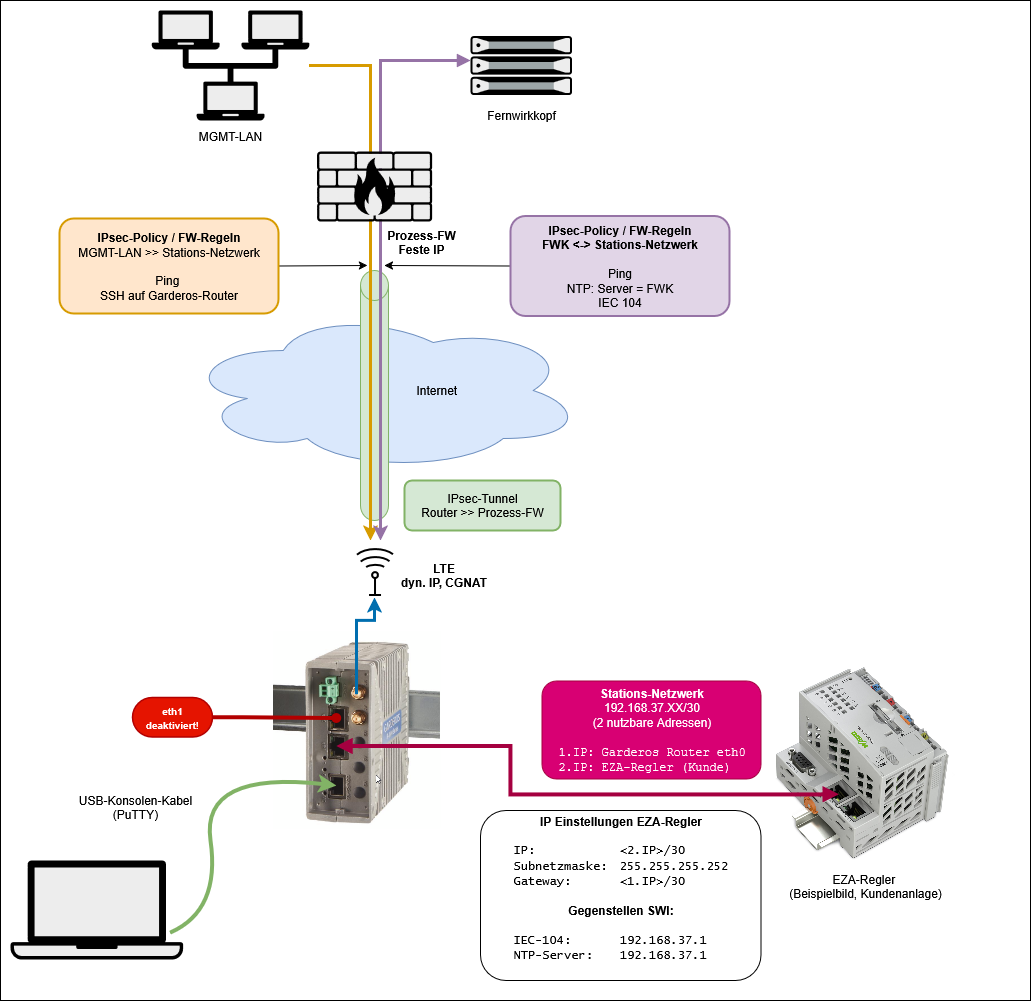
Ethernet-Schnittstelle
interface.eth.0.ip.static.0.ipv4=<Erste IP des Stations-Netzwerks/30>
interface.eth.0.name=eth0Netzwerk-Dienste
service.ntp.server.0.name=de.pool.ntp.org
service.ssh.enable=trueWWAN Verbindung (LTE)
hardware.wwan.0.name=wwan0
interface.wwan.0.apn=internet.m2mportal.de
interface.wwan.0.ip.auto.ipv4.enable=true
interface.wwan.0.name=wwan0-0LTE Diagnose (Signalstärke):
show hardware wwan wwan0 informationrouter-ISE# show hardware wwan wwan0 information
Link quality (RSSI): -70 dBm (excellent)
Aux: -91 dBm (good)
Ref power (RSRP): -96 dBm (medium)
Aux: -119 dBm (poor)
Ref quality (RSRQ): -6 dB (good)
Signal/Noise (SINR): 10 dB (medium)
Band: 1800+ (B3 20MHz)
Use technology: LTE
Current technology: LTE
Network offers: LTE
Modem supports: LTE
PIN status: disabled; upWWAN Diagnose (IP-Verbindung)
show interface wwanrouter-ISE# show interface wwan
--------------------------------------------------------------------------------
Description Value Reference
--------------------------------------------------------------------------------
Name wwan0-0
Hardware wwan0
Description
HW addr. ca:29:98:72:3f:0a
APN internet.m2mportal.de
Username ------
State UP
Up for 15m:38s
Auto IPv4 10.39.50.243/32 auto.ipv4IPsec-Tunnel Konfiguration
system.name=router-ISE
system.secret={enc3}[...]
system.timezone=Europe/Berlin
tunnel.ipsec.0.auth.psk.my-id=EEGUNNAME6
tunnel.ipsec.0.auth.psk.my-id-type=user-fqdn
tunnel.ipsec.0.auth.psk.peer-id=ILMEEG
tunnel.ipsec.0.auth.psk.peer-id-type=auto
tunnel.ipsec.0.auth.psk.psk={enc3}[...]
tunnel.ipsec.0.auto-start=true
tunnel.ipsec.0.compression=false
tunnel.ipsec.0.description=Tunnel to ILM Process Firewall
tunnel.ipsec.0.dpd.enable=true
tunnel.ipsec.0.dpd.interval=60
tunnel.ipsec.0.esp.0.encryption-algorithm=aes256
tunnel.ipsec.0.esp.0.hash-algorithm=sha256
tunnel.ipsec.0.esp-lifetime=43200
tunnel.ipsec.0.esp-pfs-group=modp2048
tunnel.ipsec.0.ike.0.dh-group=modp2048
tunnel.ipsec.0.ike.0.encryption-algorithm=aes256
tunnel.ipsec.0.ike.0.hash-algorithm=sha256
tunnel.ipsec.0.ike.0.prf-algorithm=sha256
tunnel.ipsec.0.ike-lifetime=86400
tunnel.ipsec.0.ike-version=ikev2
tunnel.ipsec.0.mode=aggressive
tunnel.ipsec.0.name=SWI
tunnel.ipsec.0.peer.name=<öffentliche IP der Prozess-Firewall>
tunnel.ipsec.0.policy.0.local-network=<Stations-Netzwerk/30>
tunnel.ipsec.0.policy.0.remote-network=<Fernwirkkopf-Netzwerk/30>
tunnel.ipsec.0.policy.1.local-network=<Stations-Netzwerk/30>
tunnel.ipsec.0.policy.1.remote-network=<Management-Netzwerk/29>
tunnel.ipsec.0.source-ip=wwan0-0:auto.ipv4
tunnel.ipsec.0.type=tunnel
user.account.0.level=15
user.account.0.name=root
user.account.0.password={sha256}[...]
user.enable.0.password={sha256}[...]IPsec Diagnose
Tunnel-Zustand anzeigen:
Pro "Policy" wird ein Tunnel angezeigt, alle sollten Status "UP" haben:
router-ISE# show tunnel
--------------------------------------------------------------------------------------------------------
IPsec tunnels:
--------------------------------------------------------------------------------------------------------
Source <-> Peer
State Local network ========= Remote network
--------------------------------------------------------------------------------------------------------
SWI
10.39.50.243 <-> 80.146.160.227
UP 192.168.37.84/30 ========= 192.168.37.0/30
10.39.50.243 <-> 80.146.160.227
UP 192.168.37.84/30 ========= 192.168.36.216/29Zur Fehlersuche Logging aktivieren
Am besten nur mit "do commit" bestätigen, nicht in startup-config schreiben!:
system.logging.0.component=net.ipsec
system.logging.0.level=debugLogbuffer ausgeben:
show logbufferEreignisse sofort im Terminal anzeigen / beenden:
terminal monitor enable
terminal monitor disableACL (Firewall-Regeln)
acl.ipv4.forward.0.action=DROP
acl.ipv4.forward.0.connection.0.state=invalid
acl.ipv4.forward.0.description=drop invalid packets
acl.ipv4.forward.10.action=ACCEPT
acl.ipv4.forward.10.connection.0.state=established
acl.ipv4.forward.10.connection.1.state=related
acl.ipv4.forward.10.description=allow established and related
acl.ipv4.forward.20.action=ACCEPT
acl.ipv4.forward.20.bidirectional=true
acl.ipv4.forward.20.dest-network=<Stations-Netzwerk/30>
acl.ipv4.forward.20.protocol=icmp
acl.ipv4.forward.20.source-network=<Fernwirkkopf-Netzwerk/30>
acl.ipv4.forward.30.action=ACCEPT
acl.ipv4.forward.30.description=NTP Verbindung zum FWK
acl.ipv4.forward.30.dest-network=<Fernwirkkopf-Netzwerk/30>
acl.ipv4.forward.30.dest-ports=123
acl.ipv4.forward.30.protocol=udp
acl.ipv4.forward.30.source-network=<Stations-Netzwerk/30>
acl.ipv4.forward.40.action=ACCEPT
acl.ipv4.forward.40.description=Allow 104 protocol
acl.ipv4.forward.40.dest-network=<Fernwirkkopf-Netzwerk/30>
acl.ipv4.forward.40.dest-ports=2404
acl.ipv4.forward.40.protocol=tcp
acl.ipv4.forward.40.source-network=<Stations-Netzwerk/30>
acl.ipv4.forward.41.action=ACCEPT
acl.ipv4.forward.41.dest-network=<Stations-Netzwerk/30>
acl.ipv4.forward.41.dest-ports=2404
acl.ipv4.forward.41.protocol=tcp
acl.ipv4.forward.41.source-network=<Fernwirkkopf-Netzwerk/30>
acl.ipv4.forward.100.action=DROP
acl.ipv4.forward.100.description=last rule, drop everything else
acl.ipv4.input.0.action=ACCEPT
acl.ipv4.input.0.connection.0.state=established
acl.ipv4.input.0.connection.1.state=related
acl.ipv4.input.10.action=ACCEPT
acl.ipv4.input.10.description=Allow ICMP
acl.ipv4.input.10.protocol=icmp
acl.ipv4.input.20.action=ACCEPT
acl.ipv4.input.20.description=Allow SSH
acl.ipv4.input.20.dest-ports=22
acl.ipv4.input.20.protocol=tcp
acl.ipv4.input.20.source-network=<Management-Netzwerk/29>
acl.ipv4.input.100.action=DROP
acl.ipv4.input.100.description=Drop everything elsePing-Diagnose
Beim Ping die IP-Adresse von eth0 verwenden!
ping 192.168.37.1 "-I 192.168.37.85"
No Comments